Governance, as defined by the IT Governance Institute (ITGI), is the “set of responsibilities and practices exercised by the board and executive management with the goal of providing strategic direction, ensuring that objectives are achieved, ascertaining that risks are managed appropriately, and verifying that the enterprise’s resources are used responsibly.” In the modern digital era, security governance has become a critical component of organizational success, ensuring that cybersecurity is not just an IT issue, but a core business priority.
At Ceelix, we provide tailored IT Security Governance consulting services, helping organizations define, implement, and refine their security governance frameworks to align with business objectives. Our approach goes beyond compliance, focusing on enabling organizations to proactively manage risk in an evolving threat landscape. We work closely with your leadership and key stakeholders to integrate security governance into your organization’s overall governance structure, ensuring that security becomes a strategic enabler of growth and resilience.
Our Services
- Defining Security Governance Frameworks
Collaborate with your board and executive management to establish a governance framework that ensures cybersecurity is aligned with business goals. We integrate security into your enterprise’s broader IT governance structure, ensuring that risk management and resource optimization are at the forefront of decision-making.
- Risk Identification and Management
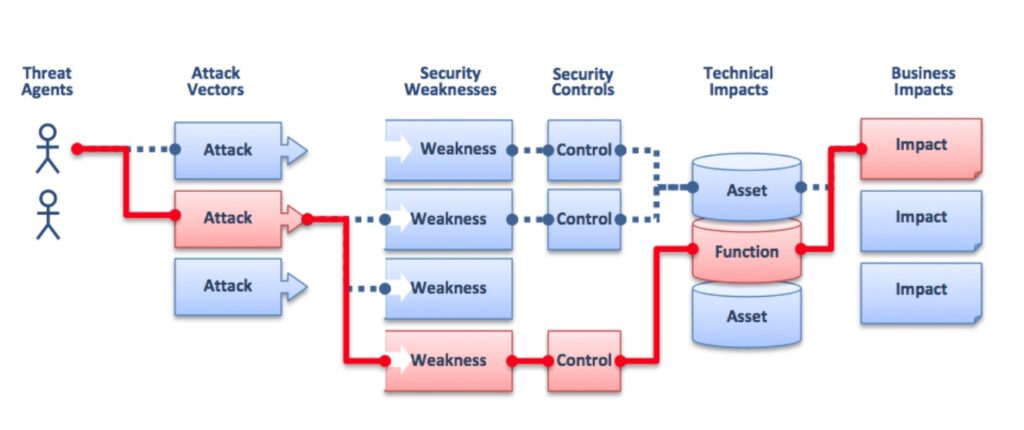
Assess the unique risks and vulnerabilities in your IT environment, leveraging industry-leading methodologies like ISO 27001, NIST, and COBIT. We provide a holistic view of your risk landscape, helping you understand how these risks impact your business objectives and how best to prioritize security efforts.
- Development and Enforcement of Security Policies
Define and implement security policies and procedures that govern everything from internal resources and third-party vendors to cloud infrastructures and mobile solutions. These policies address the full spectrum of your organization’s operations, embedding security best practices across all business processes, including the Software Development Life Cycle (SDLC) and cloud environments.
- Zero-Trust Governance and Emerging Trends
Guide organizations in adopting zero-trust architectures, where every user and device is continuously verified. This approach addresses the growing risks associated with remote work, mobile devices, and cloud adoption, ensuring that access to critical systems is secure and continuously monitored.
- Regulatory Compliance and Continuous Monitoring
Ensure that your organization stays compliant with key regulatory requirements such as GDPR, HIPAA, PCI-DSS, and ISO 27001. We implement continuous control monitoring to keep your security policies effective and up-to-date, ensuring you are always prepared for audits and evolving regulatory landscapes.
- Executive and Stakeholder Communication
Provide training and tools for your executive leadership to communicate security governance strategies effectively, ensuring full understanding and buy-in across the organization. We help frame cybersecurity as a business enabler, not just a cost center, by linking security efforts to business outcomes.
Our goal is to establish security governance that is not only robust and resilient but also flexible enough to adapt to future challenges. By focusing on business-aligned security, we ensure that your security strategy is sustainable, scalable, and proactive, keeping your organization secure in an increasingly interconnected world.