In today’s era of rapid digital transformation, Chief Information Security Officers (CISOs) are evolving from traditional IT security roles to become the central risk owners of modern organizations. As cyber breaches have impacted prominent companies across industries, security has transitioned from being just an IT issue to a critical business priority.
With the proliferation of new threats, including advanced persistent threats (APTs), ransomware, and supply chain attacks, CISOs must not only focus on protecting the most sensitive business assets but also on integrating cybersecurity with overall business objectives. IT security executives need to prioritize defending the organization’s most valuable processes while maintaining operational continuity and resilience in the face of evolving risks.
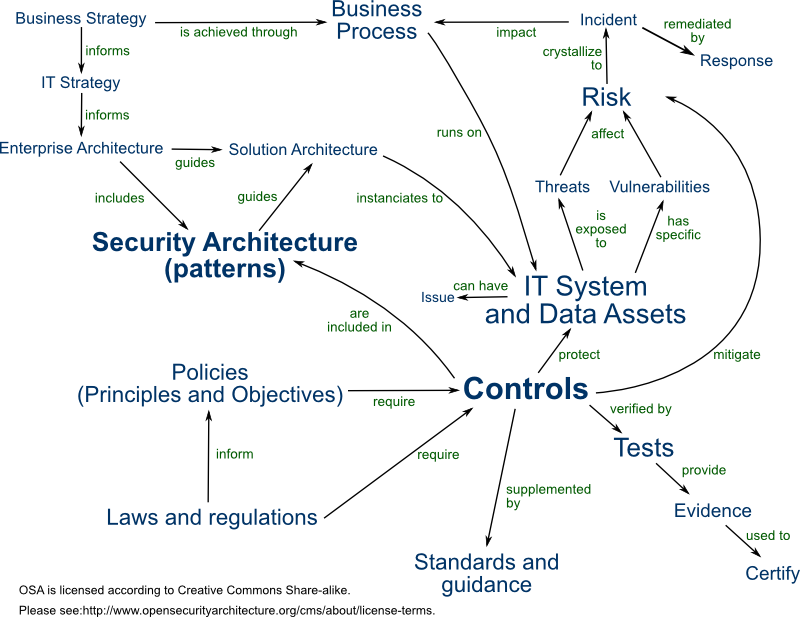
At Ceelix, we assist CISOs and IT security leaders in developing and implementing comprehensive security strategies that align with business goals, ensuring that security initiatives have the necessary management buy-in. By linking information security with business strategies, we enable organizations to mitigate risks proactively and secure executive support for security roadmaps and budgets. We specialize in crafting a strategic vision that resonates with both IT and business stakeholders, ensuring security remains a key enabler of organizational growth.
Recognizing the growing demand for flexible security leadership, we also offer Virtual CISO (vCISO) services. This model provides organizations—ranging from large enterprises to small- and medium-sized businesses—the expertise of a seasoned CISO without the need for a full-time, in-house resource. Our vCISO services offer flexibility, scalability, and cost-effectiveness, allowing your organization to have top-tier security leadership tailored to its unique needs.
In a landscape where regulatory requirements and compliance standards are constantly evolving, our CISO Advisory services also help you navigate regulatory frameworks such as GDPR, NIST, ISO 27001, and PCI-DSS, ensuring your organization stays compliant while adapting to emerging security challenges. We stay ahead of the latest trends in cloud security, AI-powered threat detection, and zero-trust architectures, ensuring that your security strategy incorporates cutting-edge technologies to keep your organization protected.
For Ceelix, securing your organization is about more than just mitigating today’s risks—it’s about anticipating and defending against tomorrow’s threats. We help CISOs sell their vision to executives by framing security not as a cost center, but as a strategic enabler of business success, driving resilience and trust in an ever-evolving risk landscape.
Our Services
Comprehensive IT Risk Assessment and Business Impact Analysis
Evaluate your organization’s risk exposure, identifying vulnerabilities across your infrastructure, processes, and technologies. We assess both internal and external threats, providing a detailed business impact analysis that quantifies risks in financial and operational terms, helping you prioritize security initiatives.
Governance, Risk, and Compliance (GRC) Framework Development and Optimization
Review and enhance your existing GRC processes or establish new frameworks that ensure your organization remains compliant with regulatory requirements such as GDPR, ISO 27001, NIST, and PCI-DSS. We integrate security and risk management into your operational processes, streamlining compliance without disrupting business activities.
Business-Aligned Security Strategy Development
Design a robust security strategy that speaks the language of business, quantifying risks, identifying solutions, and demonstrating tangible return on investment (ROI). We focus on aligning security initiatives with your overall business objectives, ensuring that security investments drive business value and growth.
Strategic Roadmap and Prioritization of Security Initiatives
Review your organization’s top security priorities and design a strategic security roadmap that addresses current and future threats. We help CISOs and security executives focus on initiatives that protect critical assets, minimize exposure, and support long-term resilience. Our roadmaps are built with flexibility in mind, adapting to evolving threats and business needs.
Development and Enforcement of Security Policies Across All Domains
Define and implement comprehensive security policies that cover internal resources, third-party vendors, business operations, and the Software Development Life Cycle (SDLC). Our policies address all facets of your organization, ensuring security is embedded into day-to-day operations and partnerships.
Cloud, Mobile, and Emerging Technology Governance
Provide expert governance for cloud, mobile, and other emerging technologies. We assist in the selection, validation, and tracking of security solutions tailored to these platforms, ensuring that your organization leverages the latest innovations while maintaining a strong security posture. Our governance models support hybrid and multi-cloud environments, ensuring compliance and security at scale.
AI-Driven Threat Detection and Zero-Trust Architecture Implementation
Incorporate cutting-edge technologies such as AI-driven threat detection and zero-trust architectures to strengthen your organization’s defenses. We design security architectures that eliminate implicit trust, enforcing strict identity and access management protocols across all users and devices.
Executive Security Communication and Stakeholder Engagement
Develop effective communication strategies to engage executives and stakeholders, translating complex security concepts into business-relevant insights. We help CISOs convey the importance of cybersecurity initiatives to leadership teams, gaining buy-in for budgets, roadmaps, and risk mitigation efforts.
Virtual CISO (vCISO) Services
Offer flexible virtual CISO (vCISO) services, providing organizations with on-demand access to top-tier security leadership. This service is ideal for businesses seeking expert guidance without the need for a full-time in-house CISO. Our vCISO solutions are scalable, cost-effective, and tailored to fit the specific needs of small, medium, and large organizations.
Continuous Monitoring and Incident Response Preparedness
Establish continuous control monitoring and incident response frameworks, ensuring your organization is prepared to detect and respond to emerging threats in real time. We implement proactive monitoring solutions and test incident response plans regularly, reducing the potential impact of breaches and minimizing downtime.