To be successful, Security and Risk initiatives must be executed as structured projects with a clear scope, timeline, and budget. At Ceelix, we leverage a strategic program/project management approach that drives GRC (Governance, Risk, and Compliance) initiatives with precision. Whether you’re defining a new security policy, ensuring compliance with evolving legal standards, or deploying cutting-edge security solutions, our tailored framework ensures alignment with both business objectives and regulatory requirements.
Our company brings strong expertise in analyzing complex technologies and provides both strategic and tactical recommendations that help organizations, from large international corporations to medium-small businesses, leverage these technologies effectively. We ensure that every recommendation is actionable, delivering maximum value regardless of your organization’s scale.
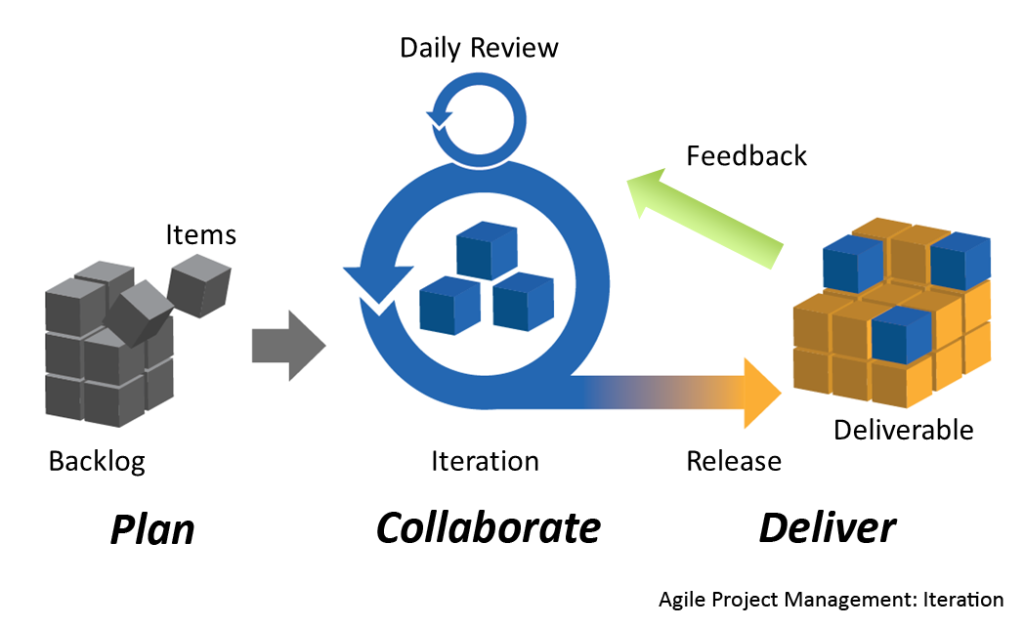
In today’s fast-evolving cybersecurity landscape, we recognize that agility and continuous adaptation are key to maintaining resilience. That’s why we emphasize agile project management methodologies to deliver rapid, tangible results in short cycles. Our flexible approach allows us to adjust to the complexity and nature of each project, ensuring that key deliverables are prioritized without compromising quality.
With our 360-degree vision—combining executive strategy, technical expertise, and security architecture—we ensure that your projects are safeguarded throughout their lifecycle. We incorporate risk and security checkpoints at every phase, proactively reducing exposure to potential threats. By integrating cloud, AI-driven insights, and CRM solutions where applicable, we elevate the maturity of your project management process, ensuring that your organization remains secure, compliant, and ready to face future challenges.
Our Services:
Organization Risk Exposure Assessments
Conduct comprehensive risk exposure assessments to identify vulnerabilities across your IT landscape, from large multinational infrastructures to smaller enterprises. We provide strategic and tactical recommendations tailored to your organization’s size and complexity.
Risk Management Framework Definition
Develop and implement robust risk management frameworks that integrate governance, risk, and compliance (GRC) practices. These frameworks are designed to be agile and adaptable to evolving industry standards and tailored to your specific business needs.
Information Classification and Protection
Design and enforce information classification policies that ensure the confidentiality, integrity, and availability of your critical data. Our expertise spans from large international corporations to SMBs, ensuring your data is protected based on its value and sensitivity.
Security Control Selection and Implementation
Identify, select, and implement the right security controls for your business, leveraging industry standards like ISO 27001, NIST, and GDPR. We ensure that these controls align with your risk appetite and business objectives while integrating seamlessly with your existing technologies.
Control Assessment, Information System Authorization, and Continuous Control Monitoring
Perform thorough control assessments to verify the effectiveness of your implemented security measures. We provide ongoing monitoring and information system authorization to maintain compliance and ensure continuous improvement in your security posture.
Disaster Preparedness and Disaster Recovery (DR) Reviews
Prepare your organization for the unexpected. Our DR services include assessments, planning, and testing to ensure rapid recovery in the face of disruptions. We align your disaster recovery strategy with cloud solutions and AI-driven insights to enhance resilience and minimize downtime.
Cybersecurity Strategy and Executive Advisory
Provide high-level strategic and executive advisory services, helping organizations design and implement a holistic cybersecurity strategy that aligns with business goals. This includes executive briefings, strategic roadmaps, and CISO-level guidance.
Cloud Security Solutions and Compliance
Evaluate, secure, and optimize your cloud infrastructure. From public to hybrid clouds, we ensure that your organization adheres to regulatory standards, with a focus on data privacy, protection, and security architecture.
AI-Driven Threat Detection and Response
Leverage artificial intelligence and machine learning to enhance threat detection, vulnerability management, and incident response. Our cutting-edge solutions allow businesses of all sizes to proactively mitigate risks in real time.
CRM Solutions with Built-In Security Controls
Implement and secure customer relationship management (CRM) systems with built-in security controls. We ensure that your CRM solution not only meets business efficiency needs but also aligns with your broader security objectives.
Compliance and Regulatory Standards Audits
Provide thorough audits for compliance with key regulatory frameworks, such as GDPR, HIPAA, PCI-DSS, and ISO 27001. Our team ensures that your organization maintains compliance while keeping up with the latest industry standards.